As we progress towards moving data networks and software to the cloud and digitally enhancing enterprise infrastructures with the capabilities of the cloud, the security threats are also amplifying in their stature. Hence, cloud security has become a problem that cannot be eradicated but only be managed. With the advancement in cloud computing technology, there have been many protection protocols to protect data from cybersecurity threats, but most proved to be not enough. This has caused a seismic shift in the way cloud security has been perceived. Building formidable fortresses surrounding data and networks is no longer adequate. Security needs to be multidimensional and deeply integrated within networks.
This blog unravels cloud security as an essential domain of cybersecurity and analyses it on multiple layers, from management to its types. Then lastly, this blog explores Microsoft’s protocols for securing the cloud.
Importance of Cloud Security
Cloud infrastructure is famous for the ease it provides in scalability. The cloud computing IaaS (Infrastructure-as-a-Service), PaaS (Platform-as-a-Service), and SaaS (Software-as-a-Service) allow businesses the flexibility of hosting a chunk or even the entire network infrastructure on the cloud, under the management of third-party hosting service providers.
Cloud security is a multi-faceted concept and includes various aspects that have their own security needs. This includes data security, identity and access management (IAM), network security, and hardware and hypervisor security.
Even though the third parties manage the applications, networks, and other aspects under a by-default security system, it is essential for organizations to understand cloud security protocols and take necessary measures to protect their data assets from inside as well.
Furthermore, the Cloud is often the target of cyberthreats due to the presence of third-party service providers in the dynamic and the consequent lack of data visibility for the organization. Therefore, while the host protects data from external threats, it is essential for organizations to secure their data assets internally.
Types of Clouds and their Security Protocols
There are three types of Cloud, which have varying security management protocols.
Public Cloud: Owned by third-party service providers, a public cloud hosts your data and network over the internet, with multiple other users. Even though it provides organizations with the leverage of storing their data anywhere which becomes difficult for bad actors to locate, but it is still considered to be least secure, due to the shared responsibility model it follows (where the host is responsible for securing the infrastructure but the organization manages data access). This model creates a lack of accountability.
Private Cloud: This is the type of cloud that stores a single organization’s data assets exclusively, which can be directly accessed by the organization. It is easier to locate your data and identify loopholes but since data is stored in a known source, it is essential for necessary actions to be taken to secure it. Security is managed by dedicated network security teams with specialized tools. Access is properly granted through secure channels like portals and self-configurations.
Hybrid Cloud: It is a system that allows organizations to store their data on public and private cloud based on the need and compliance. Organizations can move their workloads, depending on their sensitivity, back and forth on private and public clouds. Where it allows the organizations to enjoy the best of both worlds, it also increases the complexity in avoiding threats due to the enlarged attack surface and increased chances of loopholes.
Cloud Security Management
While employing cloud services, it is imperative for organizations to develop a sense of Cloud literacy to be aware of how their data is being handled and how to optimize it. Even if the host does provide security, organizations should also take steps to fortify their data empires.
A common theme in cloud security management is that the organization or the client handles the data protection and access management, while the Cloud host is responsible for providing overall security. However, for various cloud services, security management is varied.
- In Infrastructure-as-a-Service, the client is responsible for managing data protection, access management, and endpoints. They are also responsible for securing networks, systems, and applications.
- In Software-as-a-Service, the Cloud host is responsible for securing and protecting infrastructure, network security etc., whereas the user is responsible for protecting its own data, access, and endpoints.
- In Platform-as-Service, the users are responsible for data protection, access management, endpoint security, and application security.
Types of Security Practices Needed to Secure the Cloud
Cloud security is a complex system of multiple protocols and features. Let us define the important ones:
- Access Management for authorizing access to data
- Disaster Recovery for unanticipated data loss
- Network Security for securing networks through segmentation and firewalls
- Encryption for encoded data movement
- Continual Monitoring for monitoring anomalies across environments
- Password Management for authenticating passwords
Microsoft Cloud Security
Microsoft security is a rapidly growing field that works to curate solutions using Artificial Intelligence, data and automation which enable organizations to stay ahead of the threats that continue to evolve. Microsoft provides a sophisticated suite of cloud security solutions that follow multiple frameworks and protocols to provide enterprise-grade security for multiple-platform and multi-cloud data enterprises.
Microsoft Security captures more than 43 trillion signals every day to detect any malicious intents.
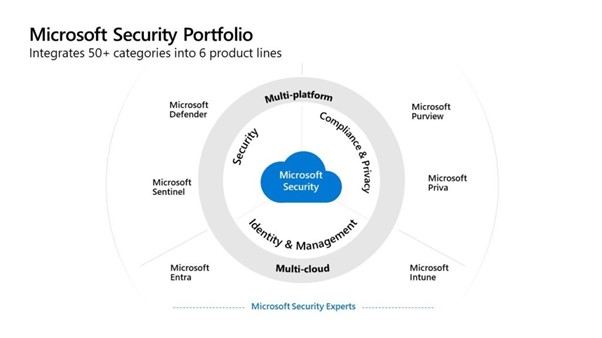
Microsoft has curated a simplified yet comprehensive security empire which consists of six product families that are intertwined. Here is a brief overview of some of them, which specifically cater to cloud security.
- Microsoft Defender for Cloud provides a centralized approach to cloud security that is end-to-end.
- Microsoft Defender for DevOps integrates security in the code, so that applications are built on a secure foundation.
- Microsoft Defender Cloud Security Posture Management provides coverage and real-time assessment capabilities to teams, across hybrid and multi-cloud environments.
- Microsoft Cloud Security Benchmark provides security recommendations for cloud workloads and secure cloud deployments.
- Azure Network Security protects networks and applications from network-based cyberattacks.
- GitHub Advanced Security enables users to build and deploy secure applications in the cloud.
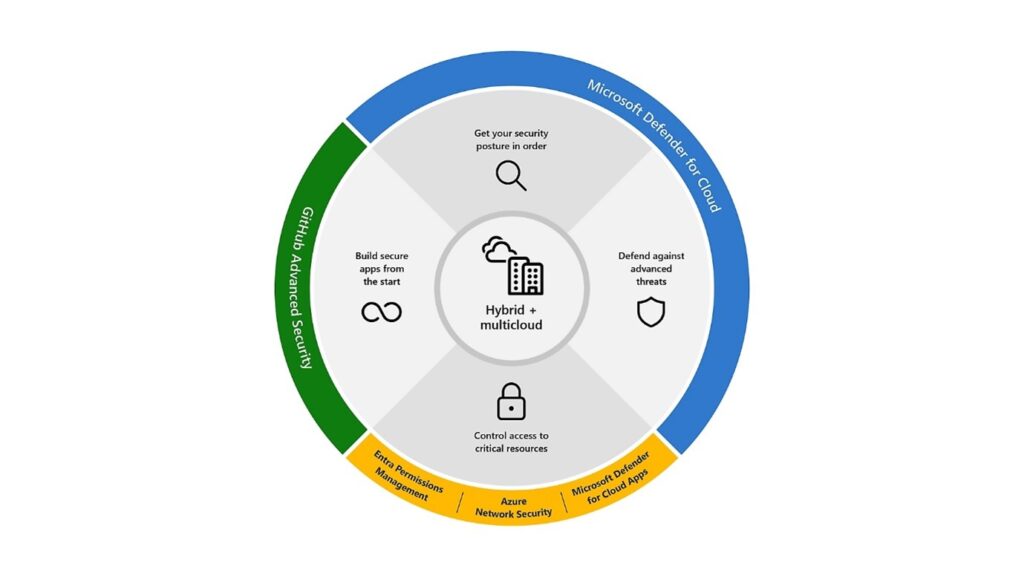
Microsoft Cloud security employs a unified platform and deep signal intelligence to help strengthen security postures for organizational cloud-based activity.
Secure Your Cloud Landscape with Dynamics Solution and Technology
Cloud is the way forward in today’s digitally advanced times. The majority of enterprises have shifted some if not all their workload and data to the Cloud. Those remaining will shift them soon. With flexibility and ease the Cloud provides, it is also the major target for all cyberthreats. Hence, it is imperative to get a hand of cloud security, so that you and your service provider can put in a con-joined effort to secure your data assets and networks from internal and external threats. Cloud security literacy also allows your organization to build governance policies that not only bring protection to your data but optimize work efficiency as well.
To get into cloud security, your business needs a team of experts to build cloud security literacy amongst your organizations. Our team of experts and consultants, at Dynamics Solution and Technology, strives to provide guidance, support, and services to not only transform businesses digitally, but to secure them against the plethora of security threats. As Microsoft’s Gold and Solutions partner, we have been digitally transforming businesses with the capabilities of a secure cloud across the Gulf and MENA regions.
Contact us and fortify your data empire with Dynamics Solution and Technology today!







