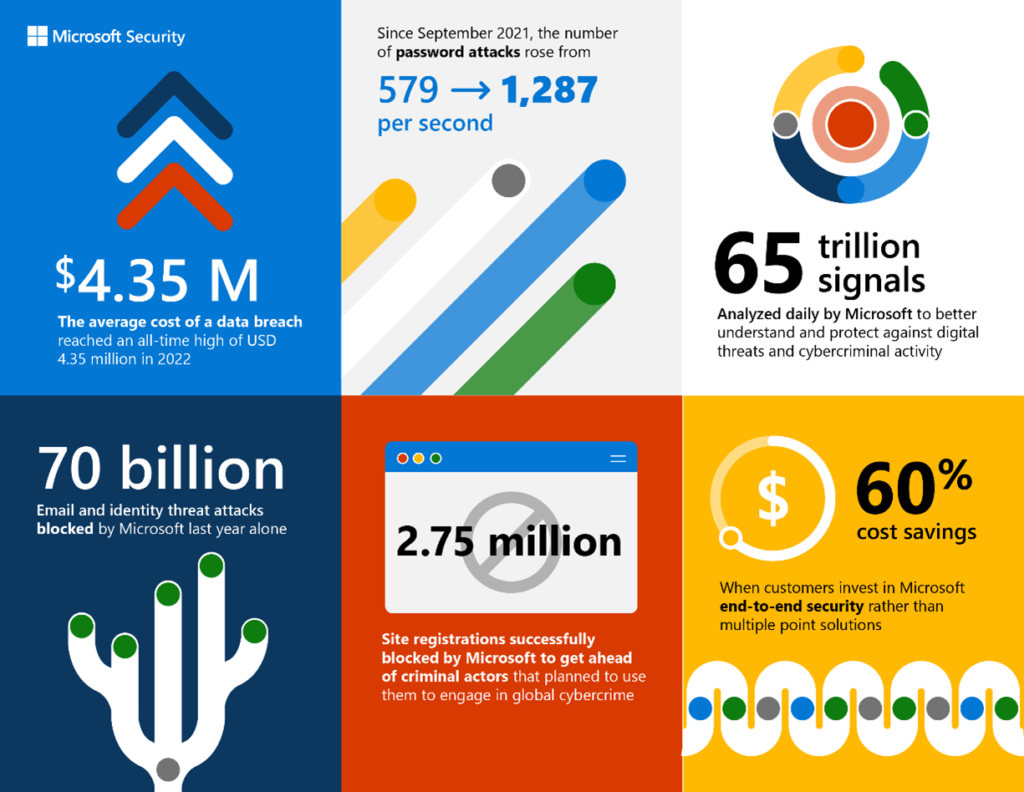
The bitter reality of our fast-paced digital transformations has been that with increased reliability on digital platforms for efficient processes, there has been a massive increase in cyberattacks as well. According to Accenture, 68% of business owners have felt that the risk of cyber-attacks has increased over time and 54% find the cyberattacks to be too potent for their tech departments’ ability to handle them.
Lately, cyber-attacks have been incredibly resolute in their nature, by constantly developing the ability to surpass any barrier that hinders them. This leaves business grappling for the sense of security they desperately need to function beyond worry. Moreover, use of AI’s capability to quickly learn and adapt is also being used in cyber-attacks. Ransomware attacks and remote work security challenges are also becoming a noticeable part of the cyber-attack landscape.
Microsoft Security emerges, in this turbulent landscape, as a trusted ally for businesses against the exceeding threats to cybersecurity. Its cutting-edge, enterprise-level solutions form together, an expansive cybersecurity umbrella from which businesses can choose the solutions that fit their needs.
Zero-Trust Framework: The Benchmark of Microsoft Security
Considering the increased potency of cyber-attacks, Microsoft has adapted John Kindervag’s “zero-trust” framework in their sophisticated set of security solutions. Where previous security architectures were designed to protect the perimeter from outside attacks, zero-trust architecture works on the belief that attacks can happen, both from outside and inside, on any level.

It is designed to extend protection from the perimeters to every email, file, and network by authenticating every transaction. Also known as ‘perimeterless security’, it helps secure every organizational device, remote access, and even third-party apps. It enables the system to verify every transaction before allowing it to happen. This ensures that no virus or malware slips in, undetected.
It works on the following core principles to maintain security:
- Verify explicitly: It encourages organizations to authenticate at every data point.
- Assume breach: Setting up end-to-end encryptions to minimize the possibility of malware spreading across, it maintains that nothing beyond the firewall is safe.
- Use least privileged access: Limiting user access according to the risk-based adaptive policies of ‘just-in-time’ and ‘just-enough-access’ for fail-safe data protection.

Security for Various Protection Needs
The cybersecurity landscape is dynamic in the sense that it has threats that constantly evolve, and attackers that target a wide range of entities. Some cyber-attacks are designed to attack identity, whereas some attack networks or even entire infrastructures. Considering the versatility of the cyber-threat landscape, the truth is that there is no one-size-fits-all security approach.
Microsoft offers a comprehensive stack of products that boldly address various cyber-protection needs. From safekeeping invaluable research to financial data, businesses can implement the security solution that suits them, from Microsoft’s security solutions. They provide specialized and enterprise-level monitoring, detection, and response capabilities for all kinds of cyber-protection needs.
Given below is a brief overview of the major cyber defense solutions provided by Microsoft. Each solution follows a different protocol, to provide security against different entities.
Microsoft Defender for Endpoint
Providing security for businesses with remote employees, Defender for Endpoint secures each endpoint asking access like end-user devices like tablets, phones, and laptops. As a cloud-based security solution, it provides comprehensive prevention, detection, investigation, and response strategies to prevent security breaches inside your organization’s endpoints and networks.
It works on the following mechanisms:
- Extensive threat and vulnerability management
- Finding and decreasing attack surfaces
- Prompt endpoint detection and response
- AI-powered investigation and remedies
- Allotting Microsoft secure scores to every device
Due to its cloud-based nature, it does not need a comprehensive infrastructure for set up. It comes with a comprehensive dashboard, which enables you to monitor your endpoints through their security scores. It even provides you with an overview of threats that have been detected and actions that are taken to mitigate them. It gives you complete visibility of your organization’s security system.
Microsoft Defender for Identity
Previously known as Azure Advanced Threat Protection or Azure ATP, Defender for Identity relies on the signals provided by your Azure Active Directory (now called Entra ID), to detect and investigate compromised IDs and insider actions that are malicious to your organization. It employs specialized analytics to observe user behavior and activities and eliminates possible attacks through kill chains.
What is Microsoft Defender for Identity?
It identifies compromised user credentials through brute force attacks, failed authentications, and other methods. It even detects lateral movements inside the networks and enables your security professionals and SecOps analysts to provide top-notch security for your organization.
Microsoft Defender for Office 365
It protects your organization’s email and collaboration tools, through the cloud. As an email-filtering service, it provides enterprise-grade protections against advanced threats that enter your organization’s network through emails. Defender for Office 365 provides protection against core threats like Business email compromises, phishing, spoofing, impersonation, and malware attacks. It effectively hunts, investigates, and works to respond to threats.
Following are the capabilities offered by Defender for Office:
- Prevention
- Detection
- Investigation and Hunting
- Response and Remediation
- Awareness and Training
- Secure Posture
Microsoft Defender comes with three level of security capabilities, each with its own set of specialized functionalities and target audience:
- Exchange Online Protection
- Microsoft Defender for Office 365 Plan 1
- Microsoft Defender for Office 365 Plan 2
Microsoft Defender for Cloud
It protects applications that are cloud-native with a specialized set of methods necessary for cloud-based application protection. It seamlessly protects processes running on Azure, hybrid and even other cloud platforms, with its integration with other Microsoft Defender Plans and Azure Arc.
Defender for Cloud combines the capabilities of following functionalities to provide top-notch protection:
- DevSecOps: Development Security Operations solutions that provide unified security at development-level across multi-cloud and multi-pipeline environments.
- CSPM: Cloud Security Posture Management solution that identifies configuration and compliance risks in cloud-based environments. It strenuously works to locate security gaps to prevent breaches.
- CWPP: Cloud Workload Protection Platform monitors and detects threats continuously for cloud workloads on various cloud environments.
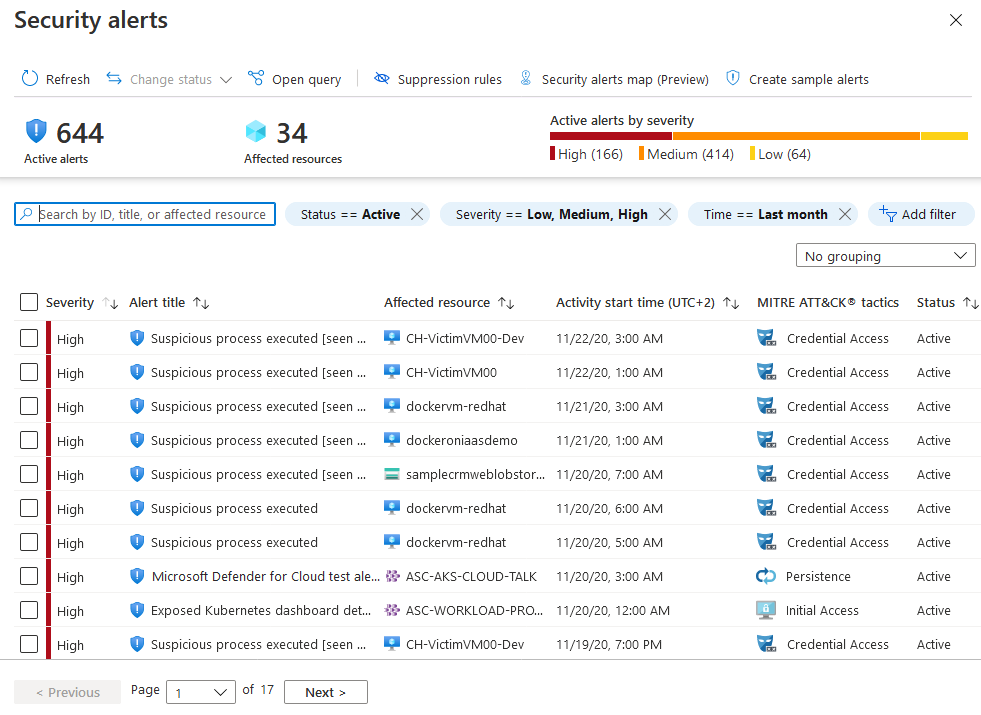
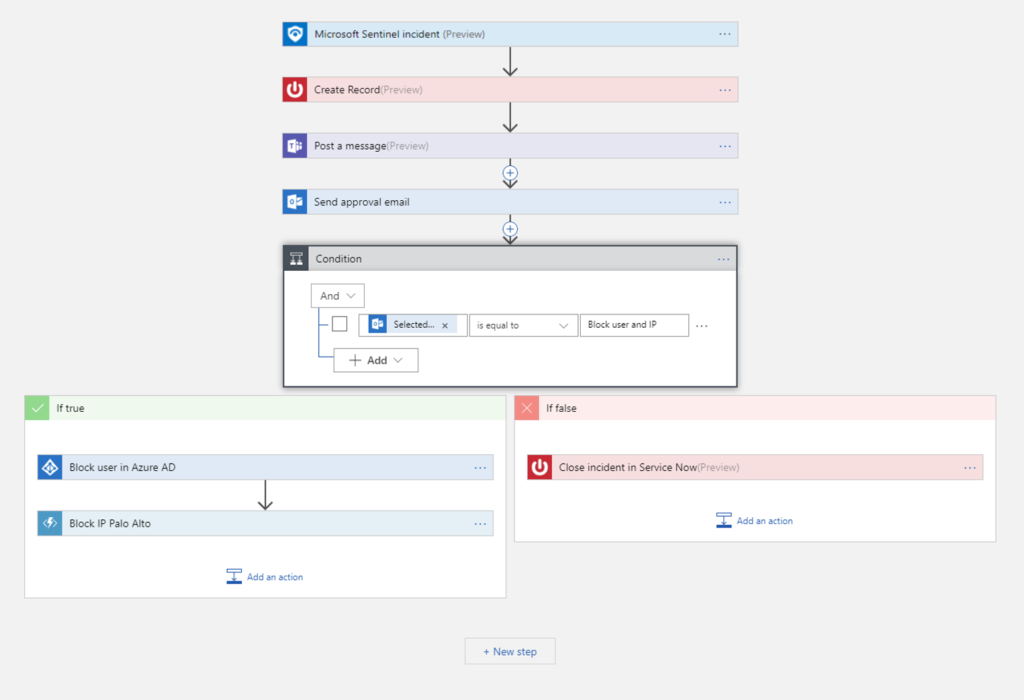
Microsoft Sentinel
As a cloud native security solution, it comes under the Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) solutions umbrella. It provides against advanced threats with security analytics and threat intelligence capabilities. It works without any comprehensive security infrastructure and is scalable to any size.
Sentinel is designed to provide your organization’s security teams with a bird eye view of the entire organization and collects data, detects, investigates, and responds to volatile threats and continuous alerts. It minimizes the noise from multiple alerts by incorporating analytics into grouping the related alerts together and filing them as incidents. It employs machine learning to map networks and work out any anomalies in them. Its main capabilities include:
- Easy and time-efficient setup
- Scores of Data connectors for convenient data ingestion
- Ingests data from cloud and on-prem environments
- Comes with a low cost and a scalable data lake
Its key components include:
- Data Connectors

- Workbooks

- Log Retention
- Analytics
- Automation Playbooks
Enhance Your Cyber Security with Dynamics Solution and Technology
Businesses need to continuously protect their data empires against ransomware or other cyber-security attacks, for sustained growth. Obliged by international data protection laws, they are also supposed to religiously protect customer data from falling into the wrong hands. For this, they need comprehensive security management solutions and seamless implementation partners for detection, investigation and fighting against the ever-evolving cyber threats.
For protecting cloud, endpoints, networks, and customer data, Dynamics Solution and Technology emerges as a formidable ally against cyber security threats. Our status as Microsoft Solutions and Gold Partner, is an ode to our commitment to excellence in implementing security and other digital solutions. We have an extended range of satisfied and protected customers in the Gulf, Mena, and European regions, who continue to enjoy the benefits of our seamless implementation services.
Contact us now for which Microsoft Security solution is suitable for your business and embattle your enterprise.








